Keeping your Linux server secure is one of the most important responsibilities of any system administrator. Among the various threats, brute-force attacks on SSH and other services are common. Fail2ban is a powerful and lightweight tool that helps protect your system by automatically banning IP addresses that show malicious signs, such as too many failed login attempts.
In this post, we’ll walk through what Fail2ban is, how to install and configure it, and some best practices for securing your Linux environment.
What is Fail2ban?
Fail2ban is an intrusion prevention software framework written in Python. It works by monitoring log files (e.g., /var/log/auth.log) for suspicious activity. If a client fails authentication multiple times in a short period, Fail2ban can block the offending IP address by updating firewall rules.
Installing Fail2ban
Fail2ban is available in most Linux distributions’ repositories. You can install it with:
On Debian/Ubuntu:
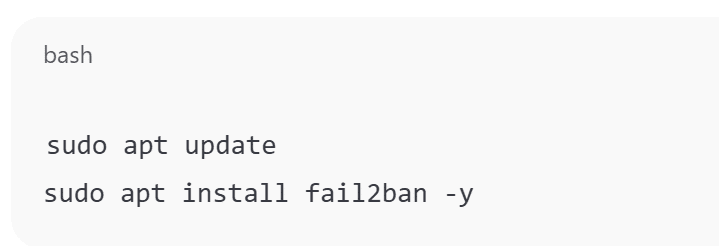
sudo apt update
sudo apt install fail2ban -y
On CentOS/RHEL:
sudo yum install epel-release -y
sudo yum install fail2ban -y
Configuring Fail2ban
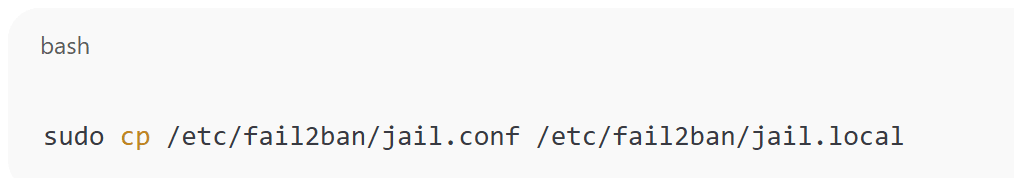
- Copy the default configuration file
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.localAlways work with
jail.localto prevent overwriting during updates. - Basic SSH Protection
Edit/etc/fail2ban/jail.localand enable the[sshd]jail:[sshd] enabled = true port = ssh filter = sshd logpath = /var/log/auth.log maxretry = 5 bantime = 3600maxretry→ Number of failed attempts before banning.bantime→ Duration (in seconds) of the ban.
- Restart Fail2ban
sudo systemctl restart fail2ban sudo systemctl enable fail2ban
Monitoring Fail2ban
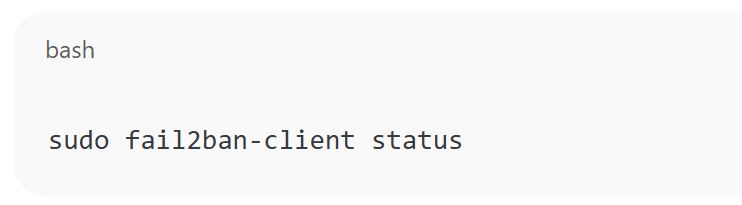
You can check the status of Fail2ban and its active jails with:
sudo fail2ban-client status
For a specific jail:
sudo fail2ban-client status sshd
Best Practices
- Use Fail2ban alongside a firewall like UFW or firewalld.
- Adjust
bantimeandmaxretryaccording to your security needs. - Protect other services (e.g., Apache, Nginx, vsftpd) by enabling their jails.
- Keep Fail2ban updated to ensure you have the latest filters.
Conclusion
Fail2ban is a simple yet highly effective tool for securing your Linux server against brute-force and bot attacks. With just a few configuration steps, you can significantly reduce unauthorized access attempts and gain peace of mind in managing your systems.
How to Secure Linux with Fail2ban (F.A.Q)
Does Fail2ban slow down my server?
No, Fail2ban is lightweight and has minimal impact on system performance.
Can I whitelist trusted IP addresses?
Yes, you can add trusted IPs under the ignoreip option in the configuration file.
Does Fail2ban only protect SSH?
No, Fail2ban has filters for many services like Apache, Nginx, and FTP servers.
What happens if I lock myself out?
You can still access your server from a whitelisted IP or by removing the ban using fail2ban-client unban <IP>.