Keeping your Linux server updated is essential for security, stability, and performance. Automating updates ensures that critical patches and security fixes are applied without manual intervention. This guide will walk you through setting up automatic updates on a Linux server using common distributions like Ubuntu, Debian, and CentOS.
Setting Up Automatic Updates on Ubuntu/Debian
Ubuntu and Debian use the unattended-upgrades package to manage automatic updates.
Step 1: Install Unattended Upgrades
sudo apt update && sudo apt install unattended-upgrades -yStep 2: Enable Automatic Updates
sudo dpkg-reconfigure unattended-upgradesFollow the on-screen prompts to enable automatic updates.
Step 3: Configure Update Preferences
Edit the configuration file:
sudo nano /etc/apt/apt.conf.d/50unattended-upgradesEnsure the following lines are enabled:
Unattended-Upgrade::Allowed-Origins {
"${distro_id}:${distro_codename}-security";
"${distro_id}:${distro_codename}-updates";
};Save and exit.
Step 4: Enable Periodic Updates
Edit the periodic updates file:
sudo nano /etc/apt/apt.conf.d/20auto-upgradesAdd or modify these lines:
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";Save and exit.
Step 5: Verify Automatic Updates
You can check if updates are being installed by running:
cat /var/log/unattended-upgrades/unattended-upgrades.logSetting Up Automatic Updates on CentOS/RHEL
CentOS and RHEL use dnf-automatic or yum-cron (for older versions) to manage updates.
Step 1: Install the Update Package
For CentOS 8 and RHEL 8:
sudo dnf install dnf-automatic -yFor CentOS 7 and older:
sudo yum install yum-cron -yStep 2: Configure Automatic Updates
Edit the configuration file:
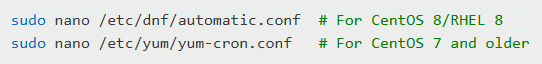
sudo nano /etc/dnf/automatic.conf # For CentOS 8/RHEL 8
sudo nano /etc/yum/yum-cron.conf # For CentOS 7 and olderSet the following parameters:
apply_updates = yesSave and exit.
Step 3: Enable and Start the Service
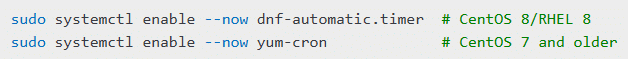
sudo systemctl enable --now dnf-automatic.timer # CentOS 8/RHEL 8
sudo systemctl enable --now yum-cron # CentOS 7 and olderStep 4: Verify Automatic Updates
Check logs with:
tail -f /var/log/dnf.rpm.log # CentOS 8/RHEL 8
tail -f /var/log/yum.log # CentOS 7 and olderConclusion
By enabling automatic updates, you can ensure your Linux server remains secure and up to date without manual intervention. However, for critical systems, consider using scheduled updates with testing to avoid potential disruptions.
How to Set Up Automatic Updates on a Linux Server (F.A.Q)
Are automatic updates safe for production servers?
Automatic updates are generally safe, but it’s recommended to test updates in a staging environment before deploying them to production servers.
Can I configure automatic reboots for kernel updates?
Yes, you can configure automatic reboots using unattended-upgrades on Ubuntu/Debian and dnf-automatic on CentOS/RHEL.
How do I disable automatic updates if needed?
You can disable them by modifying the configuration files and setting update options to no or disabling the related services.
Do automatic updates include security patches?
Yes, by default, security updates are prioritized, ensuring your system is protected against vulnerabilities.