Creating an SSH account on Ubuntu is a straightforward process, allowing users to securely access and manage their servers. This guide will walk you through the necessary steps to set up an SSH account, configure the SSH server, and secure your connections. Follow these steps to get started:
How to Create an SSH Account on Ubuntu
Step 1: Update Your System
Before setting up SSH, it’s essential to ensure your system is up-to-date. Open your terminal and run the following commands:
sudo apt update
sudo apt upgrade -y
Step 2: Install OpenSSH Server
Ubuntu comes with OpenSSH, a suite of tools for secure network communications. If it’s not already installed, you can install it by running:
sudo apt install openssh-server
To verify that the SSH server is running, use the command:
sudo systemctl status ssh
You should see output indicating that the SSH service is active and running.
Step 3: Create a New User
To create a new user who can access the server via SSH, use the adduser command followed by the username you want to create:
sudo adduser newuser
You’ll be prompted to set a password and provide some additional user information. Fill in the details or press Enter to skip.
Step 4: Add the User to the sudo Group (Optional)
If you want the new user to have administrative privileges, add them to the sudo group:
sudo usermod -aG sudo newuser
Step 5: Configure SSH Key-Based Authentication (Recommended)
Using SSH keys is more secure than using passwords. Here’s how to set up SSH key-based authentication:
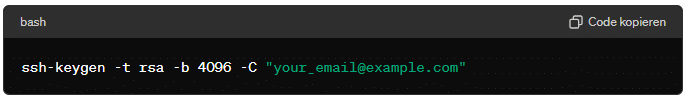
- Generate an SSH Key Pair on your local machine (not the server):
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"By default, the keys will be saved in the
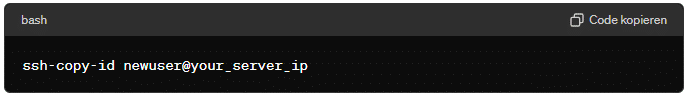
~/.sshdirectory. You can press Enter to accept the default file location and then set a passphrase for added security. - Copy the Public Key to the Server using the
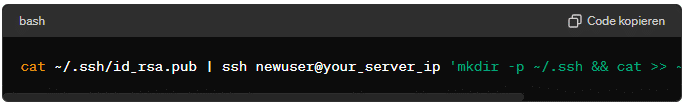
ssh-copy-idcommand:ssh-copy-id newuser@your_server_ipIf
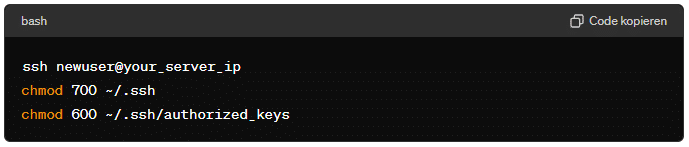
ssh-copy-idis not available, you can manually copy the public key:cat ~/.ssh/id_rsa.pub | ssh newuser@your_server_ip 'mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys' - Set the Correct Permissions on the server:
ssh newuser@your_server_ipchmod 700 ~/.ssh
chmod 600 ~/.ssh/authorized_keys
Step 6: Secure the SSH Configuration
To enhance security, you can modify the SSH configuration file:
- Edit the SSH Configuration File:
sudo nano /etc/ssh/sshd_config - Make the Following Changes:
- Disable Root Login:
PermitRootLogin no - Change the Default SSH Port (Optional):
Port 2222 - Allow Only Key-Based Authentication (Optional but recommended if you’ve set up SSH keys):
PasswordAuthentication no
- Disable Root Login:
- Save and Exit: Press
Ctrl+X, thenY, andEnterto save the changes. - Restart the SSH Service to apply the changes:
sudo systemctl restart ssh
Step 7: Connect to Your Server
You can now connect to your server using the new SSH account:
ssh newuser@your_server_ip -p 2222

Replace your_server_ip with your server’s IP address and 2222 with the port number if you changed it.
Conclusion
Setting up an SSH account on Ubuntu is essential for secure server management. By following these steps, you can create a new user, configure SSH key-based authentication, and enhance your server’s security. Regularly updating your system and monitoring your SSH access can help maintain a secure environment. Happy server management!
Create an SSH Account on Ubuntu (F.A.Q)
What is SSH and why should I use it?
SSH (Secure Shell) is a protocol for secure remote access and data transfer between computers. It’s essential for securely managing servers and encrypts your session to protect against eavesdropping and attacks.
How do I troubleshoot SSH connection issues?
Ensure the SSH service is running (sudo systemctl status ssh), check network connectivity (ping your_server_ip), verify SSH configuration (/etc/ssh/sshd_config), and confirm firewall settings allow SSH traffic (sudo ufw allow 22/tcp).
How can I enhance SSH security?
Enhance security by disabling root login (PermitRootLogin no), using SSH keys for authentication, changing the default SSH port from 22, and enabling two-factor authentication (2FA).