Limit Users Who Can Log In Using RDP
Read this article to learn about how you can ‘Limit Users Who Can Log In Using RDP’.
Sessions on Remote Desktop use an encrypted connection, so anyone listening in on the network won’t be able to see what you’re doing. However, the encryption technique utilized by older versions of RDP is susceptible to exploitation. Man-in-the-middle attacks are possible due to this flaw (the link is external).
All versions of Windows Vista, Windows 7, Windows 8, Windows 10, and Windows Server 2003, 2008, 2012, and 2016 support SSL/TLS for Remote Desktop.
Microsoft no longer provides security updates for several of the mentioned systems, so they do not conform to the requirements of the Campus network. A security exception must be made for the continued usage of unsupported systems.
Even though Remote Desktop is safer than VNC and other similar programs because the entire connection is encrypted, there are still potential security issues when granting remote access to a system with Administrator privileges. The following advice will assist you in safeguarding the computers and servers under your care when using Remote Desktop.
Limit Users Who Can Log In Using RDP
Remote Desktop allows any Administrator to connect automatically. If your computer supports numerous Administrator accounts, remote access should be restricted to just those accounts that actually need it. If you aren’t using RDP for system administration, then only enable user accounts that actually need RDP service to access it. Departments that need to remotely administer several workstations should replace the local Administrator account with a technical group and disable RDP access for the account.
- To access the Admin Tools, go to Start > Programs > Admin Tools >
2. Policy for Maintaining Safety in the Neighborhood
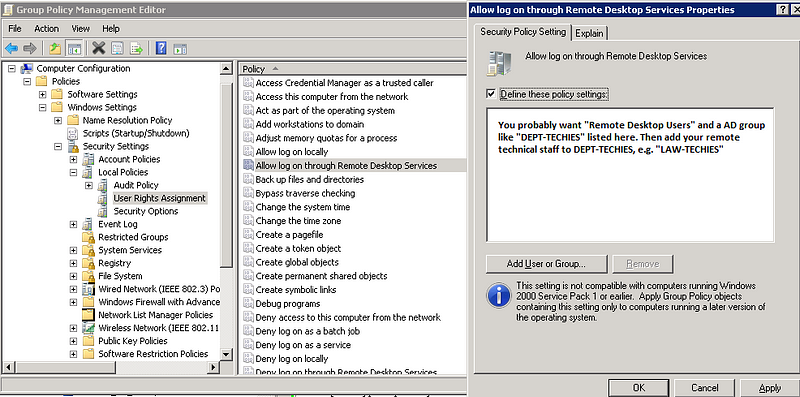
Allow login via Terminal Services” can be found under Local Policies > User Rights Assignment. As an alternative, you may say “Allow authentication via Remote Desktop Services.”
3. Just keep the Remote Desktop Users group and delete Administrators.
4. Adding members to the Remote Desktop Users group requires accessing the System settings menu.
In the Local Security Policy of a typical Microsoft OS, you will find the following entry:
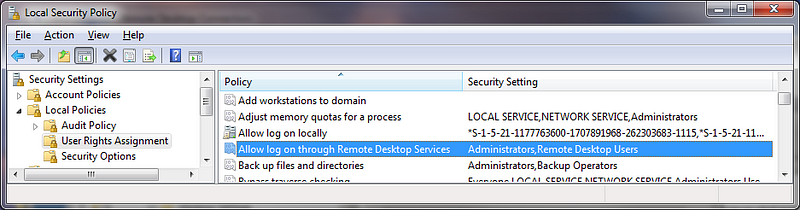
The “Administrators” group is already present here, and your “Local Admin” account is already part of this group. Although it is suggested to use a password convention to prevent the use of duplicate local admin passwords and to restrict access to these passwords or conventions, utilising a local admin account when working on a machine remotely does not adequately log and identify the user accessing the system. It is recommended that a Group Policy Setting be used to supersede the local security policy.
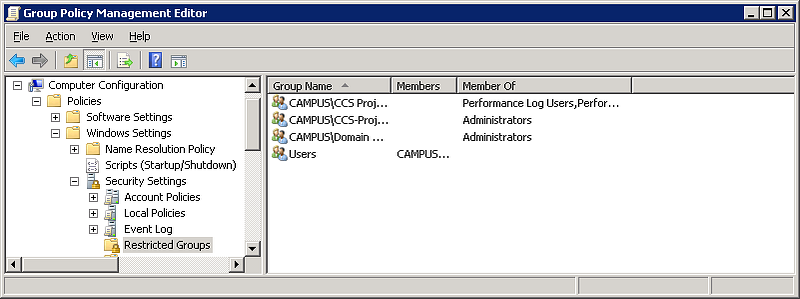
Using “Restricted Groups” within Group Policy is also useful for tightening up security around system access.
Although the “local administrator account” with RDP access has been eliminated, your techies can still access the system remotely if you use the “Restricted Group” setting to place their group, such as “CAMPUSLAW-TECHIES,” under the “Administrators” and “Remote Desktop Users” categories. Your configurations will be preserved going forward even if additional computers are added to the OU under the GPO.
CONCLUSION
After reading this article, you might have got a good idea about, Limit Users Who Can Log In Using RDP.
You can read this article to learn about, the features and functions of RDP.
You can also read this article to learn about, the security of Remote Desktop Protocol.
Visit 99rdp.com to learn about the pricing plans of different types of RDP.